Check Point uncovers massive phishing campaign targeting over 13,500 Google Classroom users globally
Written by: Check Point Research Team Save to Instapaper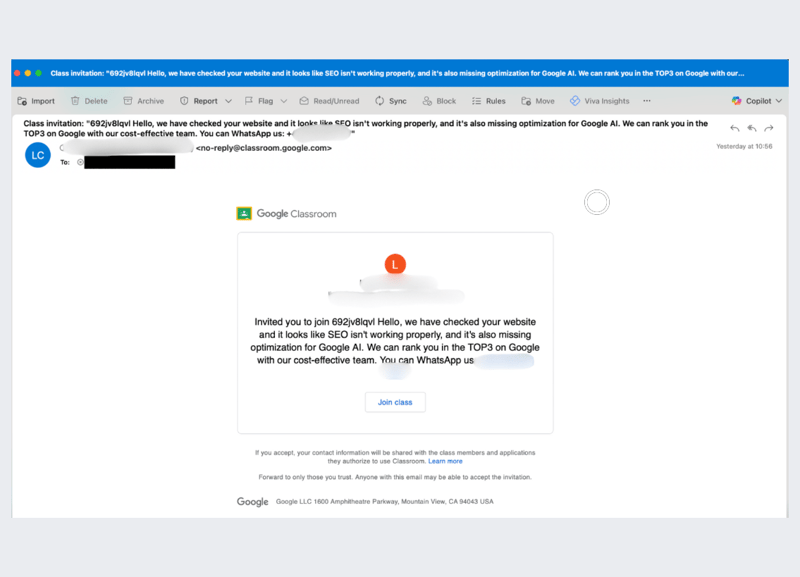
Phishing in the Classroom: 115,000 Emails Exploit Google Classroom to Target 13,500 Organisations
Check Point researchers have uncovered a large-scale active phishing campaign abusing Google Classroom, a platform trusted by millions of students and educators worldwide.
Over the course of just one week, attackers launched five coordinated waves, distributing more than 115,000 phishing emails aimed at 13,500 organisations across multiple industries. Thus far, organisations in Europe, North America, the Middle East, and Asia are being targeted.
According to Check Point's July 2025 Top Malware Report, the education sector was the most targeted globally, averaging 4,210 weekly attacks per organisation (+24% YoY). In comparison, a South African education organisation has been attacked on average 2225 times per week in the last six months.
Turning a Trusted Tool into a Threat Vector
Google Classroom is designed to connect teachers and students through invitations to join digital classrooms. Attackers exploited this trust by sending fake invitations that contained unrelated commercial offers, ranging from product reselling pitches to SEO services.
Each email directed recipients to contact scammers via a WhatsApp phone number, a tactic often linked to fraud schemes.
Figure 1: Example of the phishing email
Figure 2: Example of the phishing email
The deception works because security systems tend to trust messages originating from legitimate Google services. By piggybacking on Google Classroom’s infrastructure, attackers were able to bypass certain traditional security layers, attempting to reach inboxes at more than 13,500 companies before defenses were triggered.
Anatomy of the Campaign
- Scale: 115,000 phishing emails sent between August 6–12, 2025
- Targets: 13,500 organisations worldwide, spanning multiple sectors
- Lure: Fake Google Classroom invitations with offers unrelated to education
- Call to Action: A WhatsApp phone number, designed to move the conversation off-email and outside enterprise monitoring
- Delivery Method: Five major waves, each leveraging Google Classroom’s legitimacy to slip past filters
How Check Point Blocked the Attack
Despite the attackers’ sophisticated use of trusted infrastructure, Check Point Harmony Email & Collaboration’s SmartPhish technology automatically detected and blocked the majority of these phishing attempts. Additional layers of security prevented the remaining messages from reaching end users.
"This incident underscores the importance of multi-layered defenses. Attackers are increasingly weaponising legitimate cloud services—making traditional email gateways insufficient to stop evolving phishing tactics," says Shayimamba Conco, Security Evangelist for Check Point Software Technologies.
What Organisations Should Do
- Educate Users: Train employees to treat unexpected invitations (even from familiar platforms) cautiously.
- Deploy Advanced Threat Prevention: Use AI-powered detection that analyses context and intent, not just sender reputation.
- Monitor Cloud Applications: Extend phishing protection beyond email to collaboration apps, messaging platforms, and SaaS services.
- Harden Against Social Engineering: Be aware that attackers increasingly push victims toward off-channel communication (like WhatsApp) to evade enterprise controls.
The Bottom Line
"Attackers continue to find creative ways to exploit legitimate services like Google Classroom to gain trust, bypass defenses, and reach targets at scale. With over 115,000 emails in just one week, this campaign highlights how easily cyber criminals can weaponise digital platforms for fraud," Conco concludes.
Recognised as a Leader and Outperformer in the 2025 GigaOm Radar for Anti-Phishing, Check Point Harmony Email & Collaboration provides the advanced, layered defense needed to secure organisations against phishing attacks — even when they hide in plain sight.
About Check Point Research
Check Point Research provides leading cyber threat intelligence to Check Point Software customers and the greater intelligence community. The research team collects and analyses global cyber-attack data stored on ThreatCloud to keep hackers at bay, while ensuring all Check Point products are updated with the latest protections. The research team consists of over 100 analysts and researchers cooperating with other security vendors, law enforcement and various CERTs.
About Check Point Software Technologies Ltd.
Check Point Software Technologies Ltd. (www.checkpoint.com) is a leading protector of digital trust, utilising AI-powered cyber security solutions to safeguard over 100,000 organisations globally. Through its Infinity Platform and an open garden ecosystem, Check Point’s prevention-first approach delivers industry-leading security efficacy while reducing risk. Employing a hybrid mesh network architecture with SASE at its core, the Infinity Platform unifies the management of on-premises, cloud, and workspace environments to offer flexibility, simplicity and scale for enterprises and service providers.
Legal Notice Regarding Forward-Looking Statements
This press release contains forward-looking statements. Forward-looking statements generally relate to future events or our future financial or operating performance. Forward-looking statements in this press release include, but are not limited to, statements related to our expectations regarding future growth, the expansion of Check Point’s industry leadership, the enhancement of shareholder value and the delivery of an industry-leading cyber security platform to customers worldwide. Our expectations and beliefs regarding these matters may not materialise, and actual results or events in the future are subject to risks and uncertainties that could cause actual results or events to differ materially from those projected. The forward-looking statements contained in this press release are also subject to other risks and uncertainties, including those more fully described in our filings with the Securities and Exchange Commission, including our Annual Report on Form 20-F filed with the Securities and Exchange Commission on April 2, 2024. The forward-looking statements in this press release are based on information available to Check Point as of the date hereof, and Check Point disclaims any obligation to update any forward-looking statements, except as required by law.
Submitted on behalf of
- Company: Check Point
- Contact #: 0861777727
- Website
Press Release Submitted By
- Agency/PR Company: Kerry Botha Communications
- Contact person: Kerry Botha
- Contact #: 0832630644
- Website
Get new press articles by email
109 Press Release Articles
Pleiades Media is a strategic media communications agency specialising in travel, technology, financial and professional services
Latest from
- Check Point Software Technologies Appoints Vincent Mabaso as Head of Channel - Africa
- Global Cyber Attacks Rise in January 2026 as Ransomware Activity Increases and GenAI-Driven Data Exposure Expands
- Global Cyberattacks on Financial Institutions Jump 115% in 2025 - New Check Point Exposure Management Report Shows a Sharp Rise in Risk for Banks, Fintechs, and Payment Providers
- Check Point Software’s 2026 Cyber Security Report Shows Global Attacks Reach Record Levels as AI Accelerates the Threat Landscape
- International Day of Education - Check Point Software highlights the Importance of early cyber security education
- Check Point Introduces AI-Driven Exposure Management to Close the Cyber Security Remediation Gap
- Check Point Software Announces Eight Key Trends That Will Define Africa’s Cyber Security Landscape in 2026
- Check Point Research - Microsoft Remains the Most Imitated Brand in Phishing Attacks in Q4 2025, as Technology and Social Media Platforms Continue to Dominate
- Global Cyber Attacks Accelerate in December as Latin America Sees 26% Surge, Ransomware Jumps 60% Year-on-Year and GenAI Data Risks Expand
- Check Point Supports Google Cloud Network Security Integration
- Check Point Software Secures AI Factories with NVIDIA
- Check Point Outlines Top Christmas Scams of 2025 - How to Stay Safe
- Check Point Research for November reports increased global cyber attacks at 2,003 weekly per organisation as ransomware rises 22% and emerging GenAI threats fuel new data risks
- Check Point Software Technologies Named a Leader in Gartner Magic Quadrant for Email Security
- Hytera TETRA and broadband radios support public safety communications during the G20 Leaders Summit
The Pulse Latest Articles
- Beyond The Pit: Why Mining Partnerships Are Being Redefined (March 2, 2026)
- A Refreshing Reset For Your Tastebuds (March 2, 2026)
- Celebrating 125 Years Of Hansgrohe: Setting The Beat Of Water Since 1901 (February 25, 2026)
- Celebrate Pokémon Day At Toys R Us Menlyn On 28 Feb (February 25, 2026)
- The Great Generational Handover: Why South Africa’s Middle Managers Are The Hinge Of 2026 (February 23, 2026)
