Global Cyberattacks on Financial Institutions Jump 115% in 2025 - New Check Point Exposure Management Report Shows a Sharp Rise in Risk for Banks, Fintechs, and Payment Providers
Written by: Check Point Research Team Save to Instapaper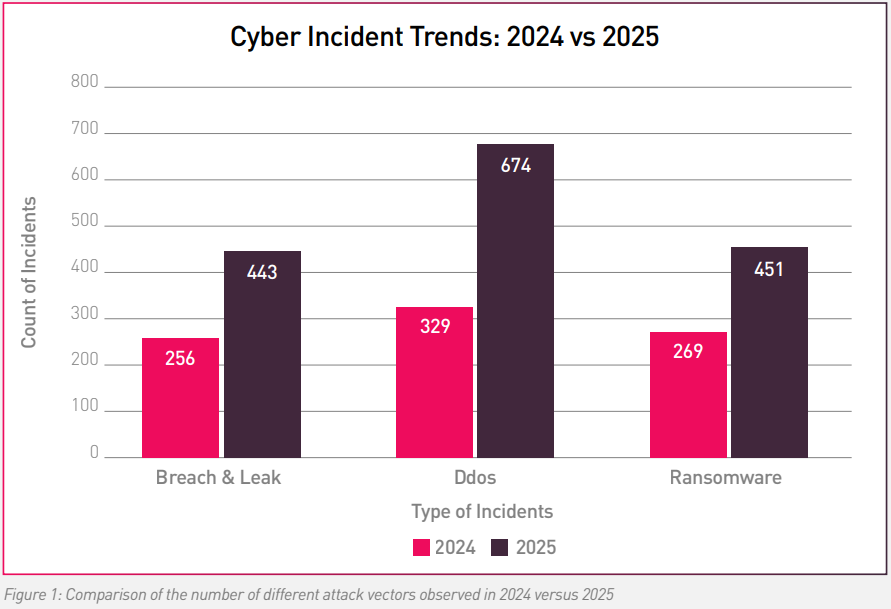
Global Cyberattacks on Financial Institutions Jump 115% in 2025: New Check Point Exposure Management Report Shows a Sharp Rise in Risk for Banks, Fintechs, and Payment Providers
Check Point's 2025 Financial Threat Landscape Report, released this week, shows that the financial sector experienced an unprecedented rise in cyber incidents in 2025, with attacks more than doubling from 864 in 2024 to 1,858 in 2025.
This acceleration reflects a dramatic shift in threat actor behavior, ranging from ideologically-motivated disruptions to commercialised cyber crime as a service.
Quick Overview of Key Trends
DDoS attacks surged 105%, driven by coordinated hacktivist campaigns targeting high visibility financial platforms and services.Data breaches & leaks jumped 73%, exposing persistent weaknesses in cloud security, identity governance, and third party ecosystems.Ransomware incidents reached 451 cases, with mature RaaS ecosystems and aggressive multi extortion tactics pushing impact to new extremes.
Download the 2025 Financial Threat Landscape here: https://checkpoint. cyberint.com/financial-threat- landscape-2026
1. DDoS Attacks Were a Geopolitical Force, Not Just a Technical ThreatDDoS attacks became the most dominant and disruptive threat in 2025, soaring from 329 incidents in 2024 to 674 in 2025, a dramatic 105% YoY increase. Unlike prior years, this surge was not primarily financially motivated. Instead, many attacks were tied to coordinated hacktivist campaigns, often aligned with geopolitical triggers. These campaigns targeted banking portals, payment interfaces, and financial service providers with the goal of denying citizen access rather than extracting money.
The attacks were heavily concentrated in regions experiencing geopolitical tension or high media visibility. Israel (112/16.6%), the United States (40, 5.9%), and the UAE (38, 5.6%), topped the list, followed closely by Ukraine (35, 5.2%) and Germany (34, 5%). This pattern reflects a strategic focus on financial entities that symbolize national resilience and global influence. The selection of targets often had more to do with political messaging than with the technical posture or defenses of the victim.
Equally notable is the centralisation of attacker groups. The majority of observed DDoS events were claimed by a small cluster of highly active hacktivist operators. Keymous+, for instance, was responsible for 121 attacks, while NoName057(16) executed 98, each operating high volume, rapid fire campaigns across multiple countries and sectors. Their tactics relied on readily accessible botnets and shared infrastructure, allowing even moderately skilled actors to scale their impact.
What makes this trend especially concerning is the shift from one-off disruptions to sustained operational pressure. Short burst attacks (sometimes dozens launched in a single day) strained financial institutions’ DDoS mitigation capabilities.
Traditional on-demand scrubbing often proved insufficient, underscoring the need for always-on detection, multi CDN routing, and layered defense strategies that can withstand prolonged waves of ideologically driven disruption.
2. Identity Weaknesses Continue to Undermine the Financial CoreData breaches and leaks rose sharply from 256 incidents in 2024 to 443 in 2025, highlighting systemic weaknesses across identity governance, cloud environments, and third-party integrations. Unlike DDoS attacks, which are designed for quick, public disruption, these intrusion campaigns were largely stealthy. They often involved long-term access, silent data exfiltration, and delayed disclosure.
The United States remains the most heavily targeted geography, with 177 breach and leak cases, representing 40% of all global incidents. India (31 cases) and Indonesia (24) followed as emerging hotspots, largely due to rapidly expanding financial ecosystems and growing exposure to cloud-based operations. These markets' high digital transaction volumes and extensive financial infrastructures offer attackers both scale and valuable data.
One of the most striking findings is that 33% of breach incidents were attributed to unknown actors. This reflects a notable evolution, increased operational security, short lived infrastructure, and a shift toward decentralized identities and burner accounts. The growing difficulty of attribution suggests attackers are becoming more sophisticated in masking their footprints across the deep and dark web.
Threat actors specialising in data compromise also remain active. Groups such as Breach Laboratory (43 incidents) have built reputations for exploiting misconfigurations, buying initial access credentials, and leveraging leak sites for extortion campaigns. However, even more concerning is how misconfigurations, such as open storage buckets, permissive access controls, unmonitored API endpoints, continue to appear across financial networks. These issues persist despite significant industry investment, underscoring the need for identity-centric security models, automated cloud scanning, and strict access governance.
3. Ransomware Ecosystems, Multi Extortion, and Persistent Targeting of High Value AssetsRansomware remained one of the most severe threats to financial institutions, with 451 incidents recorded in 2025, up from 269 the prior year. This increase reflects both the maturity of ransomware as a service (RaaS) operations and the growing sophistication of extortion strategies. Attackers are no longer satisfied with encrypting data; they now combine encryption, exfiltration, public shaming, and direct pressure on executives and customers.
Financial institutions remain attractive targets because of their low tolerance for downtime and high operational dependency on interconnected systems. The United States again topped the list with 196 ransomware cases (43.5%), followed by South Korea (31, 6.9%), the United Kingdom (22, 4.9%), and Canada (16, 3.5%). The geographic spread maps closely to economies with large digital banking footprints, making them prime candidates for maximum extortion leverage.
Threat activity is heavily concentrated among a small set of actor groups, many of which operate sophisticated affiliate programs. Qilin led with 83 incidents (18.4%), followed by Akira (37, 8.2%) and Clop (19, 4.2%). These groups rely on shared tooling, highly modular malware, and well-organized affiliate networks that scale operations quickly and efficiently. Their tactics include exploiting VPN vulnerabilities, abusing stolen credentials, and targeting third-party service providers to gain footholds into multiple victims simultaneously.
The rise of multi-extortion ransomware has significantly heightened the impact. Beyond encrypting critical systems, adversaries now increasingly threaten regulatory exposure, customer notification, reputational harm, and even targeted harassment of senior executives. This broader pressure creates cascading financial and reputational consequences that extend well beyond the initial security incident. As a result, traditional backup and recovery strategies, while still critical, are no longer sufficient on their own.
How Does 2026 Look for the Financial Industry?The financial sector is entering a new era of cyber risk, one defined by campaign-driven DDoS, stealthy data compromise, and high impact ransomware ecosystems. The sharp escalation across all major attack categories in 2025 underscores the growing sophistication, automation, and global coordination of threat actors operating across both criminal and ideological motives. Financial institutions must move rapidly toward intelligence-led, identity first, and always-on security models to stay ahead of these threats.
While the target of attacks was the US and then on India, Indonesia, South Korea, the U.K., Brazil, and LATAM markets, Africa cannot afford to be complacent.
"When it comes to Africa, the financial sector often sets the trend in both deploying digital services to customers and maintaining a relatively mature cybersecurity posture. However, this report highlights that despite this maturity, financial institutions remain heavily impacted by cyberattacks. This underscores the reality that offensive security capabilities are evolving faster than organisations can deploy appropriate defences," says Hendrik de Bruin, Head: Security Consulting - Africa, Check Point Software Technologies.
"Further evidence also suggests that we will continue to see an increase in both the sophistication and the volume of attacks. More adversaries are leveraging Artificial Intelligence to enhance their campaigns, while geopolitical tensions continue to rise," he adds
The financial sector should therefore continue to invest in cybersecurity solutions such as Continuous Threat Exposure Management (CTEM). This approach enables organisations to become more proactive by identifying, verifying, and prioritising security risks—such as stolen credentials, vulnerabilities, and misconfigurations—before attackers have the opportunity to exploit them.
Download the full 2025 Finance Threat Landscape Report here: https://checkpoint. cyberint.com/financial-threat- landscape-2026
Submitted on behalf of
- Company: Check Point Software Technologies
- Contact #: 0105949795
- Website
Press Release Submitted By
- Agency/PR Company: Kerry Botha Communications
- Contact person: Kerry Botha
- Contact #: 0832630644
- Website
Get new press articles by email
109 Press Release Articles
Pleiades Media is a strategic media communications agency specialising in travel, technology, financial and professional services
Latest from
- Check Point Software Technologies Appoints Vincent Mabaso as Head of Channel - Africa
- Global Cyber Attacks Rise in January 2026 as Ransomware Activity Increases and GenAI-Driven Data Exposure Expands
- Check Point Software’s 2026 Cyber Security Report Shows Global Attacks Reach Record Levels as AI Accelerates the Threat Landscape
- International Day of Education - Check Point Software highlights the Importance of early cyber security education
- Check Point Introduces AI-Driven Exposure Management to Close the Cyber Security Remediation Gap
- Check Point Software Announces Eight Key Trends That Will Define Africa’s Cyber Security Landscape in 2026
- Check Point Research - Microsoft Remains the Most Imitated Brand in Phishing Attacks in Q4 2025, as Technology and Social Media Platforms Continue to Dominate
- Global Cyber Attacks Accelerate in December as Latin America Sees 26% Surge, Ransomware Jumps 60% Year-on-Year and GenAI Data Risks Expand
- Check Point Supports Google Cloud Network Security Integration
- Check Point Software Secures AI Factories with NVIDIA
- Check Point Outlines Top Christmas Scams of 2025 - How to Stay Safe
- Check Point Research for November reports increased global cyber attacks at 2,003 weekly per organisation as ransomware rises 22% and emerging GenAI threats fuel new data risks
- Check Point Software Technologies Named a Leader in Gartner Magic Quadrant for Email Security
- Hytera TETRA and broadband radios support public safety communications during the G20 Leaders Summit
- Check Point Launches 2025 African Perspectives on Cyber Security Report
The Pulse Latest Articles
- Beyond The Pit: Why Mining Partnerships Are Being Redefined (March 2, 2026)
- A Refreshing Reset For Your Tastebuds (March 2, 2026)
- Celebrating 125 Years Of Hansgrohe: Setting The Beat Of Water Since 1901 (February 25, 2026)
- Celebrate Pokémon Day At Toys R Us Menlyn On 28 Feb (February 25, 2026)
- The Great Generational Handover: Why South Africa’s Middle Managers Are The Hinge Of 2026 (February 23, 2026)
