Mobile testing can make or break small screen experience
Testing should not be viewed as a ‘quick fix’, but an integral part of the DevOps process, says Inspired Testing.
The proof that considerable advances have been made in mobile testing is evident when one compares the user experience a decade ago to present time. From frustratingly slow and difficult to navigate, mobile interfaces are now coming into their own, providing millions of seamless and happy encounters.
Does this mean mobile testing has finally found its groove?
Well, yes and no. Yes, because the small screen platform is finally being understood as a discrete medium that requires specific testing skills and expertise. Mobile testing is now an area of specialisation. And no, because the diversity of content, continuous updates and the plethora of devices on the market at any given time – with their associated operating and application software – create a constant challenge to mobile testers, and their clients, to provide a fast, error-free and fluid user experience.
With what do we test it, dear Liza?
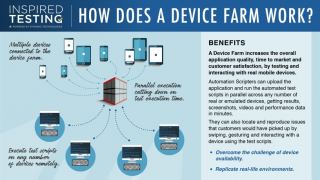
“One of the biggest tribulations for companies wishing to test their software on mobile devices is access. The number of makes and models available can make it a cumbersome, expensive and ongoing process,” says Jacques Fouché, CEO of software testing firm Inspired Testing.
Cloud-based public device farms provide a range of mobile devices and offer a useful rental service, but they have some drawbacks. Firstly, it can get very expensive, especially for larger corporates that have a wide range of services they need to cover. Larger organisations often require 24/7 access to the devices for a prolonged period of time. “Public device farms are more suitable for smaller companies that have a couple of apps they want to test, but this also depends on their risk profile,” explains Fouché.
Another option is cloud-based private device farms, where you strategically procure your own devices and either house them in your own data centre within the business, or with an outsourced provider. Either way, you have 100% access to the devices at any time, without having to pay a rental fee. ‘Strategically procure’ means you buy certain models within a brand, as testing on one device will give you similar screen real estate on four or five other devices. “This option is good for high-volume device users requiring stringent levels of security, such as companies in the financial technology space,” says Fouché. Companies that strive to achieve a high frequency of continuous integration and deployment would also do well to consider a private device farm, as this will give them unrestricted access to the devices.
Houston, we have lift-off… or not
Once the challenge of how to access devices for testing purposes has been solved, the process of testing begins. This is where companies can really come unstuck, says Lloyd Dignan, Director: New Business, Inspired Testing. “Whether it’s a new release or an update, a complete retest is the only solution. There is a perception that once you have released your app or launched your Web site, any subsequent updates will not be as critical. Many big players have discovered the hard way that this is not the case. No company is immune to crashes and errors. To avoid this, testing should be viewed not as a ‘quick fix’, but an integral part of the DevOps process,” he explains.
Understanding which devices your market uses is also critical to the testing process. Tapping into the information streams available, such as market research, Google Analytics and your marketing engine will provide insights into the make and model of devices accessing your site or app, from which you can extrapolate technical data. Also bear in mind that device usage differs significantly from country to country. For example, in the UK, the majority of 18-35-year-olds have the latest iPhone. In Romania, the Samsung Galaxy J5 is the most popular phone, while Chinese brands Tecno and Infinix are big brands in Nigeria. “Keeping current with devices and operating system updates is one of the main challenges facing companies,” says Dignan.
One thing mobile users across markets, countries and continents do have in common is intolerance to poor app and Web site performance. “There is absolutely no loyalty,” says Dignan. “If an app crashes or takes too long to load (between four and eight seconds on average), the user will move on – and even delete the app before they go.” Because there is such fierce competition, there is significant pressure on companies to go live as soon as possible. “The opportunity for mobile is massive, but organisations have to make sure their systems and applications are fully tested – and the errors fixed – before they release. Errors become compounded with each new update and it gets harder to fix each time,” explains Dignan.
A changing landscape
There are clear statistics that show a massive transition from user access via desktop and laptop to mobile devices (including tablet), while the consumption of data has moved significantly from laptop to mobile. Mobile devices are not only used to access apps; they are becoming the platform of choice to access Web sites. This makes Web site testing as important as app testing, as an estimated 63% of users worldwide now use their mobile devices to access Web sites. There is much more likelihood of someone completing their cart on a phone than on a laptop or desktop. In addition, says Dignan, the emergence of responsive Web sites – Web sites that shrink down and respond to the size of the screen – made mobile browsing much easier, while many companies are now releasing apps to augment their Web sites, to provide an interactive user service. Progressive Web applications that look and load like ‘normal’ Web pages, but offer the functionality of an app, are also becoming standard practice.
These shifts are creating massive opportunities in the mobile space, and consequently, a significant explosion in mobile testing, says Fouché, particularly in industries such as fintech, logistics and retail. Automated mobile testing has become an area of specialisation in itself, and mobile testing is no longer a sub-set of testing, but a category in its own right.
-- END --
About Inspired Testing
Inspired Testing’s disruptive onshore offshore model offers a revitalised alternative to outdated offshore models. With a scalable pool of 250+ expert SQA professionals in the UK and South Africa, the company’s strength lies in knowing how to structure, execute and automate testing. Importantly, our ISO 27001 certification and its alignment to the UK/EU GDPR (General Data Protection Regulation) ensures full protection of critical personal data. Inspired Testing uses a unique combination of experience, technique and blended onshore offshore delivery capabilities to provide expert software testing across most platforms, devices and environments. www.inspiredtesting.com
Inspired Testing is a wholly owned subsidiary of Dynamic Technologies, a software and technology group with 1 000+ staff and thirteen group companies across the UK and South Africa providing a diverse range of technology solutions, digital services and related core competencies. Our group companies comprise DVT (which includes the DVT Academy), Inspired Testing, DotModus, Cloudsmiths, IndigoCube, Blue Pencil Consulting, Dynamic DNA, Blue Pencil Creative, Emerald Consulting, Dynamic Talent, EventSmiths and Swarm. www.dynamic-tech.com
Real-Time Analytics Sheds Light on African Power & Water Challenges
Cape Town, May 16: FuseForward, a provider of cloud and analytic solutions, is demonstrating the benefits real-time analytics can deliver to African utilities during the African Utility Week conference and exhibition.
Held from 14-16 May in Cape Town, South Africa, African Utility Week is the leading conference for African power, energy and water professionals. FuseForward’s Founder and CEO, Mark Damm, is excited about the opportunity to provide analytic solutions that shed light on the challenges faced by utilities in Sub-Saharan Africa.
“Utilities in Africa face a range of issues, many of which affect their ability to meet basic demands for water and electricity,” says Mark. “We know that the availability of reliable and complete data is critical in order for utilities to find solutions to their challenges.
Data from IoT devices and smart meters can help, but developing the technology required to ingest, store and make sense of this information is a barrier for many resource-strapped utilities.” FuseForward’s cloud platform provides a secure, reliable way for utilities to store, aggregate and analyze data from their IoT and smart devices, delivering the comprehensive performance information utilities need within a single interface.
Example utility challenges that FuseForward can address include:
- Demand management: Data from devices and external sources can be used to predict peak electricity or water usage times, enabling better management of resources.
- Preventative maintenance: Deteriorating infrastructure can often be the cause of outages in Sub-Saharan Africa.
By analyzing sensor data from equipment and infrastructure, utilities can obtain real-time maintenance alerts, preventing outages before they occur.
With the event set to close today, Mark is optimistic about the future for the industry, and the role FuseForward can play. “We’ve had a chance to hear first-hand about the challenges facing utilities and are looking forward to the opportunity to help solve them. Not only do analytic solutions in this sector have the ability to provide business improvements for utilities, they also play a role in improving the delivery of power and water across Sub-Saharan Africa—and that’s something our team is very enthusiastic about!”
About FuseForward
FuseForward is an AWS Advanced Technology Partner and Select Consulting Partner that provides secure cloud environments and analytic solutions for critical infrastructure providers and public agencies. Headquartered in Vancouver, Canada, we serve customers around the world from our offices in South Africa, Europe and North America.
For more information visit www.fuseforward.com
Media Contact: Wendy Scott at +27 83 270 7765 or This email address is being protected from spambots. You need JavaScript enabled to view it.
CloudOne.mobi secures major investment to boost its cloud-based business solutions
Cape Town-based CloudOne Technologies Pty Ltd, trading as CloudOne.mobi, has announced that it closed two funding rounds totalling R34m at the end of 2018. The investors include Investec Private Capital, through its Emerging Companies mandate. The investment will be used to help scale out and grow the business more aggressively. CloudOne.mobi was founded in October 2014 with the mission of re-inventing the Point Of Sale (POS) experience.
Founder and CEO Dana Buys has successfully started and sold a number of software businesses since launching his first business while studying at the University of Cape Town in the early 1980s. Subsequently a hospitality business owner, among other interests, he became frustrated with poor levels of technology, particularly related to POS. Buys is passionate about customer service and wanted a solution that would improve the speed and accuracy of serving customers.
"Speed and accuracy deliver a win-win for both business and its customers,” he says. “Happy customers spend more and spread the good news via word of mouth. Accurate orders reduce costly mistakes and improve profitability. It’s hard to beat if you can make the solution easy-to-use and affordable to own!” He continues, “There is massive opportunity to deploy affordable Cloud and mobile technology in Sub-Saharan Africa. The Cloud solutions model allows us to eliminate many of the headaches experienced by SME businesses which often lack strong IT skills. We develop the , keep the systems up to date, manage the databases and integration to external solutions, perform regular backups, and enforce security.”
CloudOne.mobi has developed an advanced cloud-based Point of Sale solution called TallOrder for SME businesses across the hospitality, retail and service segments. TallOrder delivers Cloud benefits, along with robust offline capacity to deal with the relatively slow, less reliable and costlier Internet prevalent throughout emerging markets. Buys explains that similar solutions developed in the United States and Europe assume an always-on, fast and low-cost Internet which is not yet the case in Africa and other developing markets.solution
CloudOne.mobi says TallOrder is easy to deploy, easy to learn to run, and operates on Microsoft Windows, Apple's iOS, and Android devices. It is designed for traditional point of sale stations, tablets and even smartphone-sized devices. The system supports mobile use, which boosts the speed and accuracy of customer service. "TallOrder replaces expensive upfront license and installation fees with low monthly or annual fees, based on the number of devices in use. This opens the market to many businesses which previously could not afford nor cope with the older technology" says Anna Groenewald, COO and co-founder at CloudOne.mobi.
According to Meiring de Wet, Chief Technology Officer at CloudOne.mobi, "SME companies by themselves will never generate enough data to be as truly useful as Big Data. We have built TallOrder in a way that allows us to aggregate the small data coming from SME businesses into Big Data".
“This investment is an important opportunity for CloudOne.mobi to expand our software developments and allow us to rapidly scale our marketing and sales efforts and increase our future partnership opportunities,” stated Groenewald. Learn more about CloudOne.mobi and their hero products TallOrder Point of Sale and PageMan Digital Signage on their website, https://cloudone.mobi/ or contact them at This email address is being protected from spambots. You need JavaScript enabled to view it./ +27 (0) 728630116
Risky solutions you use to protect your organisation
Securing corporate perimeter is one of the basic measures a company should take to make sure that nothing threatens its workflow. Although many enterprises are not successful at keeping their network intact. Some organisations
- think of safety instruments only after an incident occurs
- are simply not aware of all the risks
- have been using or are going to use services which might expose them to additional risks
- focus their attention on hackers neglecting internal threats
- are worried about compliance violations and forget about other less relevant but by no means less detrimental breaches
And some happen to trip on almost each of the steps. Computer systems of Johannesburg-Lewiston Area Schools were affected by a ransomware. The insurance provider covered the financial damage although the school wasn’t prepared to deal with the issue and the Superintendent appeared to be unaware of basic cyber incidents that might happen to any organisation.
About a month ago a school technology consultant informed the administrator of a problem impeding file opening. The investigation determined that the attack was coming from Germany.
The school doesn’t store employees’ and students’ data on the servers so personal details weren’t compromised. The school network isn’t fully backed up and corporate devices were impacted significantly making staff members bring their own computers and gadgets — a decision fraught with peril.
Some measures were taken after the violation occurred. The school is going to upgrade antiviruses, create a cloud-based storage securing its protection and focusing their concern on being resistant to ransomware attacks. Anyway, using a Google doc system might keep offenders from harming the server but online storages pose some risks which demand as much attention.
Cloud, antivirus, MSSP, interdicting data transfer
As we can see the organisation:
- reacted to the necessity of improving the risk management mechanisms after a violation had occurred
- claimed to be not prepared to the incident not only due to being insufficiently equipped but also due to being simply unaware of what might happen to their servers
- decided to update its antivirus and relocate the information to online storages overlooking such risks as cloud misconfiguration and data leak as well as the fact that antivirus is only one of many ways to fight cyber attacks
- put all the efforts to ensuring perimeter protection from hackers and didn’t think of securing their environment from insider threats
Besides online storage and antivirus, there are tools and technologies which
- protect you from incidents while compromise your confidentiality or undermine strategic risk assessment
MSSP provides you with an experienced staff aware of every detail about recent threats and regulations and using most relevant tools to safeguard your workflow. But third party consultants know little about your corporate culture, your employees and business processes which have been tuned and customized to fit your needs. Opting for MSSP you should keep in mind that you delegate network monitoring to an intermediary who you are not familiar with and that everything is going to be displayed to the service provider bringing your privacy to zero.
Tools interdicting data transfer, preventing information from being printed or uploaded to a flash drive keep sensitive details within the company’s limits but don’t make you more knowledgeable about your corporate environment and staff members’ communication. Behavior risk management includes possibility of seamless monitoring which facilitates in-depth investigation.
- are nearly inefficient when not integrated as a bundle which comprises a comprehensive solution for both external and internal safety
If you implement a one-sided approach to risk management and address only external threat preventive measures you might flatten your security fortification you have been working on to ensure that your company can fight any offender. Internal control systems are indispensable — they allow you to cover any kind of inside violation thus making you prepared to regulate incidents the source of which is within the company’s perimeter. Employee monitoring software increases significance of that shield which took you efforts to defend your organisation from external attacks.
The core issue many organisations have to recognise is that they are healing symptoms instead of trying to cure provoking factors. A breach occurs, a company fixes it, a problem is solved — a common security misconception. Such a short-sighted tactic keeps you exposed to multiple yet undiscovered threats and makes your efforts look like masking whereas they should be about securing. While you are covering a gap there might appear another one which requires mending with the help of a different instrument.
Tools shielding your perimeter from external attacks will not ensure that your data is intact within the corporate network. Access delimitation will not help when information gets lost, stolen or deliberately leaked. Cryptography will make you theft- or lossproof although it doesn’t guarantee the safety of your documents if someone is willing to disclose their details. The most recent automated compliance management software will put you at the needed level of conformity but focusing on preventive measures that allow you to avoid the biggest penalty will make you let your guard down regarding some latent internal threats.
Today’s CSRs are under pressure to do a lot more for customers. Is your IT department equipped to deliver what they need?
Discerning, informed, and connected.
With a multitude of choices in the marketplace, multiple buying channels, and instant access to information, today’s customers have never been more empowered, or more demanding. They’ve come to expect the ability to deal with a company on their own terms, very often opting for the convenience of self-service. So, when they do take the time to call a company, it’s usually because they have an immediate need—an issue they want resolved right away, and to their complete satisfaction.
An effective customer service representative (CSR) plays a critical role in meeting those expectations. No detail—from the CSR’s speaking voice to the quality of the sound on the line—is too small. And, the CSR must possess a certain kind of temperament, professionalism, and skill—but these alone are not enough. Answering the phone is just the start. Today’s customer service representative (CSR) listens, understands, and acts upon a customer’s needs with skill, rigor and thoughtfulness. Every minute, every day, the CSR needs to demonstrate that they have the customer’s best interests in mind, while presenting the company in the best possible light.
In fact, for the customer, the CSR doesn’t just represent the company, they are the company. Their job is to completely engage with the customer to provide the most informed advice, support, and guidance.
Problem-solver, diplomat, expert, empathizer: a CSR needs to be all these, and more. How can you help equip them for success?
A headset is a vital tool to the CSR. When it’s performing as expected, it’s barely noticeable. But if a setting needs to be adjusted or updated, it’s immediately noticed—and IT needs to handle it, right away. For companies with hundreds or even thousands of CSRs, it has meant a lot of effort for IT to manage their needs efficiently—until now.
Plantronics has a solution that helps IT monitor, manage, and maintain headsets. Plantronics Manager Pro is a cloud-based management tool that results in effortless management for IT, helping ensure users always have well-maintained headsets that enable them to confidently engage with customers, and ultimately improve the customer experience.
Now available in South Africa, find out how Plantronics Manager Pro can help make headset management effortless. Learn more here.
About Plantronics Plantronics is an audio pioneer and a global leader in the communications industry. We create intelligent and adaptive solutions that support our customers’ most important needs: experiencing and facilitating simple and clear communications while enjoying distraction-free environments. Our solutions are used worldwide by consumers and businesses alike and are an optimal choice for open office environments. From Unified Communications and customer service ecosystems, to data analytics and Bluetooth headsets, Plantronics delivers high-quality communications solutions that our customers count on today, while relentlessly innovating on behalf of their future. For more information visit www.plantronics.com.za
Are you prepared for a data disaster?
If all your company’s data was wiped out today, could you cope?
It’s a fact that crime and theft in South Africa are putting businesses’ resiliency at risk daily. This is in combination with natural disasters such as flooding or fire, and global cyber-attacks such as ransomware.
Yet, few businesses are truly prepared for an unforeseen disaster which could wipe out their essential data.
Too often, companies’ backup systems are ineffective in the face of disaster, especially if the backups are on-premise or not automated.
Other challenges include capacity limitations, network issues and bandwidth constraints, and the maintenance of backup systems.
The rise of cloud computing has presented a solution to these challenges, and off-site Backups-as-a-Service (BaaS) and Disaster Recovery-as-a-Service (DRaaS) offer a variety of benefits.
Services such as Cloud Backup by DataKeepers offer a more affordable, secure alternative to traditional backups, with easy deployment, friendly tech support, and scalability.
Cloud Backup is based on three tiers:
1. Backup: This may seem obvious, but having reliable backups is the very first step in preparing for any disaster. For larger backups and slower Internet connections, you can send a drive with your data to DataKeepers to upload for you as an initial seed. Backups thereafter will only be incremental on the data that has changed, saving you bandwidth and upload time.
2. Continuity: If disaster should strike, Cloud Backup’s unique ‘Spin Up In The Cloud’ feature allows you to spin up a virtual instance of your device and continue working over a remote session while replacing your failed hardware. For quick access, your data is easily accessible via a web console for download or instant restore to a different device.
3. Restore & Recovery: Restore your data directly from the cloud to your new platform or have DataKeepers deliver replacement hardware with your data just as it was. Large-scale recovery can also be performed by means of a “reverse seed” and your data can be couriered back to you, saving on bandwidth and recovery time.
DataKeepers offers 24/7 support and monitoring, as disasters can strike at any time, and the company continuously monitors all backup statuses and immediately notifies you of any issues.
As DataKeepers has its own local infrastructure, your backup data also never leaves South Africa. You know exactly where and with whom your data is stored, giving you peace of mind, knowing your data is secure and that it complies with local data security policies.
Data Security
Your backups will also be fully encrypted by enabling industry-standard AES256 encryption, which takes place before the data even leaves your device.
The encryption key is set by the user and cannot be retrieved in any way.
The transfer of the data is then further encrypted by SSL while uploading to their cloud storage, with the option of storing a second copy on-site.
Ransomware Protection
Another key feature of Cloud Backup’s service is the Real-Time Ransomware Protection that blocks a ransomware takeover in its tracks – at no additional cost.
Ransomware has crippled many companies worldwide, and once data is encrypted, it's near impossible to 'decrypt' – even after paying the ransom amount.
Plans and Pricing
DataKeepers’ pricing is structured quite differently to the conventional “storage + per device” model available on the market.
The professional plans have no limit on the number of users or devices (Desktop, Server, Linux, Mac, and Mobile) and DataKeepers only takes into the account the amount of storage used.
Additionally, DataKeepers includes plug-ins for MS SQL, Exchange, Office 365, and a number of virtualisation platforms such as Hyper-V and VMware at no additional charge.
Resellers and Partners
DataKeepers also focuses on building long-term customer relationships with a white-label Partner Program that caters for resellers who wish to sell Backup-as-a-Service to their customers.
With Cloud Backup by DataKeepers, there is no reason to take any risks.
Originally founded in 2002 and having rebranded in 2016 to DataKeepers, the Cape Town-based company has the knowledge and experience to provide you with exactly what you need when it comes to virtual servers, backup services, private cloud, and other hosting services.
For more information on the services and features offered, visit datakeepers.co.za or call them on 021 556 9999.
Integr8, Extreme and Duxbury launch ‘networking-on-demand’ service in South Africa
In a ground-breaking move, three leading local IT companies have banded together to launch South Africa’s first pay-per-use, fully-managed, corporate networking solution which will be targeted at developing markets throughout Africa.
Dubbed EasyLAN, the solution has been developed under the auspices of a joint venture agreement between the local arm of Extreme Networks, a leading worldwide software and services-led networking solutions company, Integr8, a local ICT management specialist, and Duxbury Networking, a leading value-added distributor with a continent-wide footprint. EasyLAN is a standardised managed service allowing customers to take advantage of the latest networking technologies and modern hardware and software offerings without having to invest in a costly in-house infrastructure.
EasyLAN will enable businesses to manage their network services via an online portal in real time,” explains Andy Robb, chief technology officer at Duxbury Networking. “There is no upfront capital investment needed as customers pay only on a per-port-used basis. Moreover, EasyLAN ensures that the latest technological developments from Extreme Networks are incorporated as part of the deal.”
Robb says the EasyLAN solution represents a definitive evolution of cloud-based technologies and is the spearhead of the joint venture’s new cloud networking initiative within the African business arena.
“In the same way as the cloud boosted the management of data centres, so the concept of networking-on-demand, as supported by EasyLAN, will be a boost for corporate networks," he notes.
Martin May, regional director (Africa) for Extreme Networks, confirms that EasyLAN will be able to transform an organisation’s network infrastructure through the incorporation of next-generation technology.
“A key advantage of EasyLAN will be a significantly simplified corporate IT landscape, allowing organisations to fully optimise their investments in networking resources while benefitting from the technical expertise of three of SA’s most prolific networking technology exponents.”
He says EasyLAN provides the ultimate in flexibility and simplicity, allowing users to migrate their IT budget spending from capital to operational expenditure by removing the bulk of their hardware.
“EasyLAN will assist businesses to keep abreast of the massive increases in data traffic on their networks, a growing percentage of which is video traffic which is putting mounting pressure on legacy networks.
“Today, network managers should be tasked with quickly responding to changing business demands by making the corporate network more responsive to user demands, more scalable and more automated.”
In this light, May says businesses also need improved control over their networks in order to optimise costs and remain competitive in the fast-paced business environment. According to Bennie Strydom, Chief Sales Officer at Integr8, EasyLAN allows users to moderate their network usage, scaling up or down depending on the ‘ebb and flow’ of business needs, as they pay only for the ports they use on a month-to-month basis.
“The solution allows users to free up the time, money and costly resources usually associated with running, maintaining and supporting their networking infrastructures, putting them to better use to develop new, innovative business strategies and solutions,” he adds.
Strydom says the pay-per-port offering allows users to customise and configure their LAN ports to accommodate their organisations’ specific work force. “Because users only pay for what they use, it's a risk-free model.” “The EasyLAN solution is supported by comprehensive hardware maintenance and device management services which allow for 24x7 monitoring of users’ networks with an immediate response from a technical support team should a problem arise,” Strydom continues.
“Proactive monitoring means the customer will receive best-in-class support and maintenance from a team of highly trained and proficient technicians. Importantly, EasyLAN will give users’ technical teams the space and budget to focus on their own core strengths which include the growth of the business going forward,” he concludes. [ENDS]
For more information contact: Luned Lira
Marketing Manager
Duxbury Networking
tel: +27 (0) 11 351 9800
fax: +27 (0) 11 646 3079
cell: 072 159 5840
email: This email address is being protected from spambots. You need JavaScript enabled to view it.